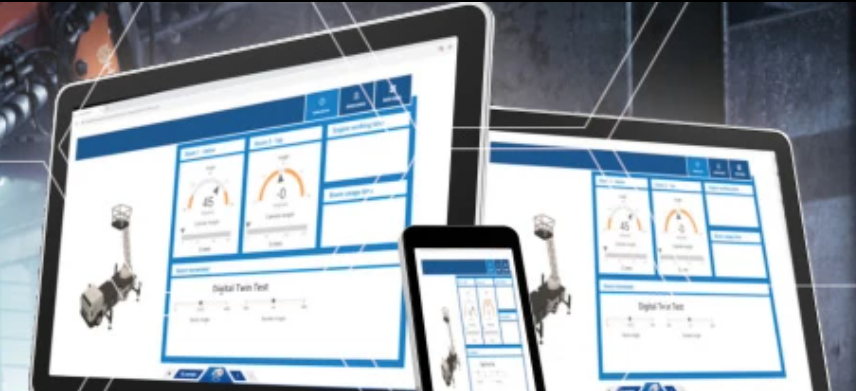
Modern fleet management solutions like Epec’s GatE and GlobE tools and cloud-based services use IoT technologies to manage the operation of connected vehicles. The benefits include higher utilization and lower maintenance costs. But, there are risks too.
When a system lacks sufficient security “bad actors” can gain access to data and potentially even take control of vehicles on the system. This makes cybersecurity for IoT fleet management systems a topic of vital importance for fleet managers.
Fleet Management and the IoT
Vehicles used in construction, agriculture, mining, and similar industries are good candidates for an IoT fleet management solution. As high-value machinery, it’s important to maximize utilization, minimize operating costs, and prevent theft while ensuring safe and reliable operation.
An IoT solution takes the form of data capture ECUs mounted on the vehicle, interfaced to both the vehicle CAN bus or other data sources, and an IoT remote monitoring and access unit. Cellular communication to this access unit gathers data on selected vehicle systems that are subsequently stored in the cloud for access via a tool like GlobE.
The Cybersecurity Risk
In 2010, Stuxnet showed that cybersecurity is about more than just running antivirus software on laptops and desktop PCs. Any kind of computing device can be attacked and compromised, and anything internet-connected is potentially vulnerable.
Readers might recall that the Stuxnet attack used USB flash drives to deliver a virus to systems not on the internet. The point here is that it wasn’t an internet connection that caused the problem, although that may provide a way of accessing other systems.
An IoT fleet management system has multiple points an attacker can target. Cellular communications are an obvious area, but any part of the system from the vehicle CAN bus to the cloud servers is a potential target.
Once an attacker gains access to a fleet management system there are many things they could do. These range from the innocuous — looking around “because they can” — to gathering data on vehicle operations for competitive advantage and even taking control of vehicles and holding them “hostage.”
Cybersecurity for IoT Fleet Management Systems
Fleet managers have a host of tools at their disposal to prevent cyber-attacks and to minimize their impact should they occur. Taking a high-level view, three of the most important aspects to evaluate are:
- Understand the risk
- Review the provider’s security
- Review internal cybersecurity practices
Understand the Risk
Attacks can be both physical and remote. A physical attack is one where the attacker has direct access to the IoT hardware or vehicle. They might for instance be able to plug into one of the ECUs or the IoT remote access unit.
A remote attack is one carried out from a distance. Examples would be intercepting cellular communications with the IoT device and gaining access to files on the cloud server.
Review the Provider’s Security
Quiz the company providing the IoT fleet management system about how they keep their system secure. Key points to look for are:
- Encryption of cellular communications
- Location of the cloud servers used (some countries, such as Finland, are considered more secure than others)
- Where the hardware and software are manufactured
Review Internal Cybersecurity Practices
Given that attacks can come from both inside and outside the organization, (disgruntled current and former employees are a common attack vector), make sure to follow cybersecurity best practices. The main points to consider include:
- Restrict equipment access (hardware and software) to only those who should be operating equipment or uploading, downloading, and reviewing files
- Use strong passwords, assigned to individuals and not teams or departments
- Remove access rights promptly when employees leave or are terminated
- Discourage, or better yet, disable, use of flash drives in USB ports
- Make sure employees understand their duties and responsibilities when it comes to maintaining cybersecurity
Developer and User Responsibilities
An IoT fleet management solution has many benefits for businesses operating construction, agricultural, or other types of vehicular equipment. However, it’s essential to recognize that, as with other business transactions conducted over the internet, security must be paramount.
Cybersecurity for IoT fleet management systems begins with the developer and extends through the end user’s enterprise. Developers must follow best practices and should be able to explain and demonstrate the security features built into their product. Encryption, password protection, and cloud security are just some of the points to explore.
Furthermore, partnering with a security-aware developer/vendor does not exempt the end-user from responsibility. As with any other business system, physical assets and data are best protected by following cybersecurity best practices.
To learn more about the security features of the HydraForce IoT fleet management solution, click below.